Tipp
Falls du die Google Cloud Platform nicht nutzt, kannst du die Bereitstellung in einer anderen Bereitstellungsumgebung automatisieren.
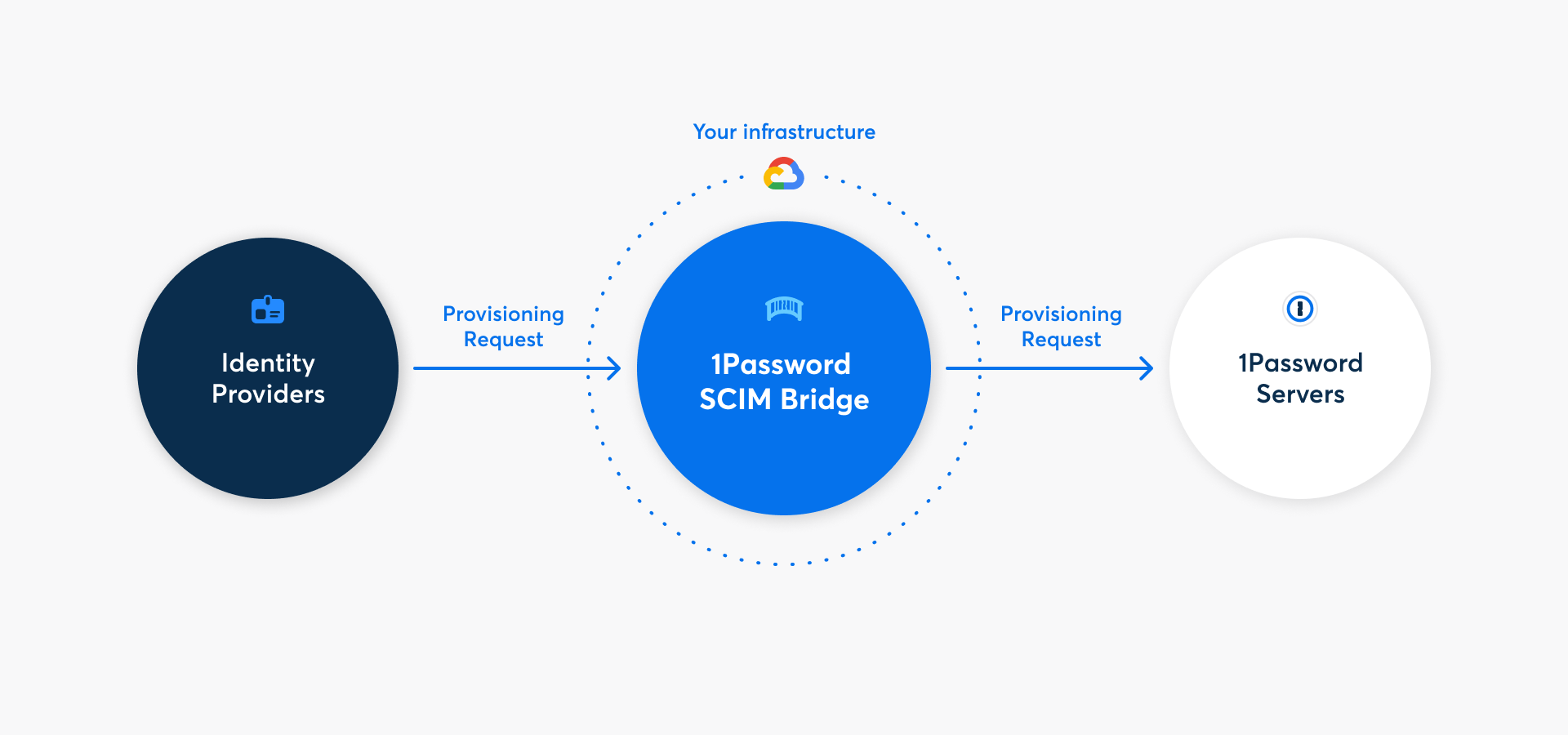
Mit 1Password Business kannst du viele gängige Verwaltungsaufgaben mit der 1Password SCIM-Bridge automatisieren. Es nutzt das SCIM-Protokoll (System for Cross-Domain Identity Management), um 1Password mit deinem bestehenden Identitätsanbieter wie Google Workspace, JumpCloud, Microsoft Entra ID, Okta, OneLogin oder Rippling zu verbinden.
Schritt 1: 1Password SCIM-Bridge auf der Google Cloud Platform bereitstellen
Falls du noch kein Google Cloud Platform-Konto hast, erstelle eines. Dann folge diesen Schritten.
1.1: Ein Projekt erstellen
Die SCIM-Bridge muss innerhalb eines Projekts bereitgestellt werden. Um ein Projekt zu erstellen:
- Besuche die Seite Ressourcen verwalten und wähle Projekt erstellen.
- Gib einen Projektnamen ein. Wenn du Teil einer Organisation bist, wähle sie aus.
Wenn du deine Organisation nicht auswählen kannst, wende dich an den Administrator deiner Google Cloud Platform-Organisation.
- Klicke auf Erstellen.
Nachdem das Projekt erstellt wurde, kannst du die SCIM-Bridge konfigurieren.
1.2: 1Password SCIM Bridge konfigurieren
Besuche 1Password SCIM Bridge auf dem Google Cloud Platform Marketplace und wähle Konfigurieren. Wenn du dazu aufgefordert wirst, wähle das zuvor erstellte Projekt aus.
Tipp
Wenn du die Meldung „Kubernetes Engine Admin-Rolle ist erforderlich“ siehst, ignoriere sie. Die Meldung verschwindet, nachdem du einen Cluster erstellt hast.
Fülle die folgenden Felder aus:
- Cluster: Wähle einen vorhandenen Cluster aus oder erstelle einen neuen Cluster. Wenn du einen neuen Cluster erstellst, aktualisiere die Seite nach dessen Erstellung.
- Namespace: Verwende den bereitgestellten Standard. Wenn du bereits eine Anwendung im Cluster hast, kannst du auch einen neuen Namespace namens „1password“ erstellen.
- Name der App-Instanz: Verwende den bereitgestellten Standard.
- 1Password-Anmeldeadresse: Deine 1Password-Anmeldeadresse. Zum Beispiel:
example.1password.com
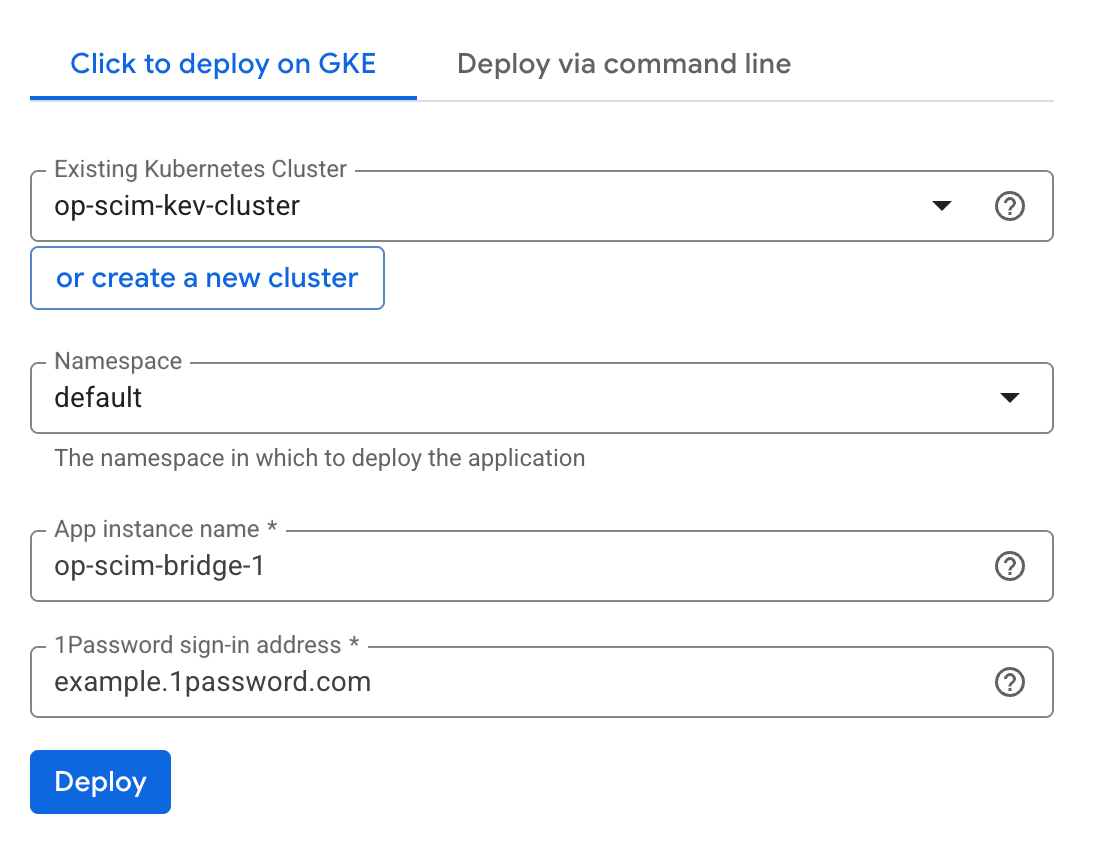
Wenn du fertig bist, wähle Bereitstellen aus. Nachdem die SCIM-Bridge bereitgestellt ist, siehst du die Anwendungsdetails.
1.3: 1Password SCIM Bridge einrichten
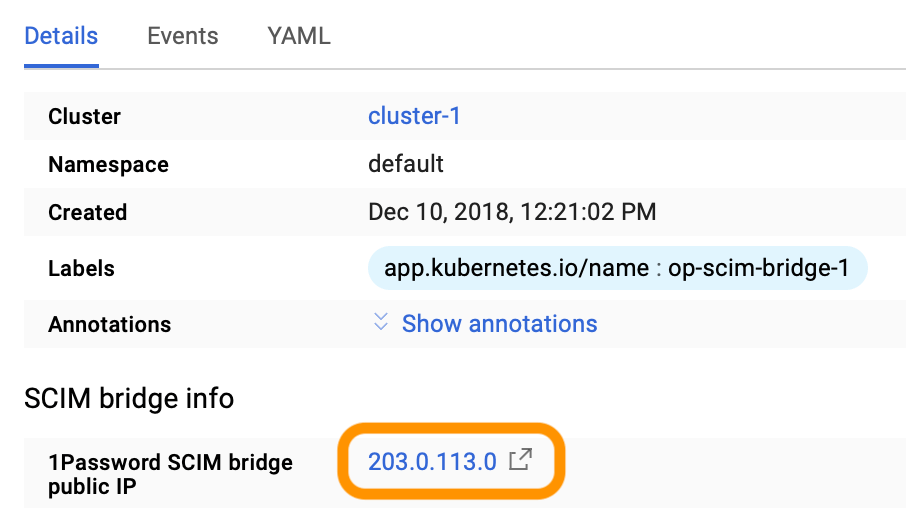
Im Abschnitt „SCIM Bridge-Info“ der Anwendungsdetails beginnt die „1Password SCIM-Bridge öffentliche IP“ mit 10 (z. B. 10.11.255.255), was eine private IP-Adresse ist.
Aktualisiere die Seite, bis sich die IP-Adresse in eine öffentliche IP-Adresse ändert, die nicht mit 10 beginnt.
Bevor du die SCIM-Bridge mit deinem 1Password-Konto verbinden kannst, musst du außerdem Folgendes tun:
- Konfiguriere einen DNS-A-Eintrag für deine gewählte Domain und leite ihn auf die IP-Adresse deines Load Balancers um. Zum Beispiel:
scim.example.com. - Warte, bis die DNS propagiert ist.
Navigiere dann zu deiner SCIM-Bridge-Domain.
Schritt 2: Verbinde die SCIM-Bridge mit deinem 1Password-Konto
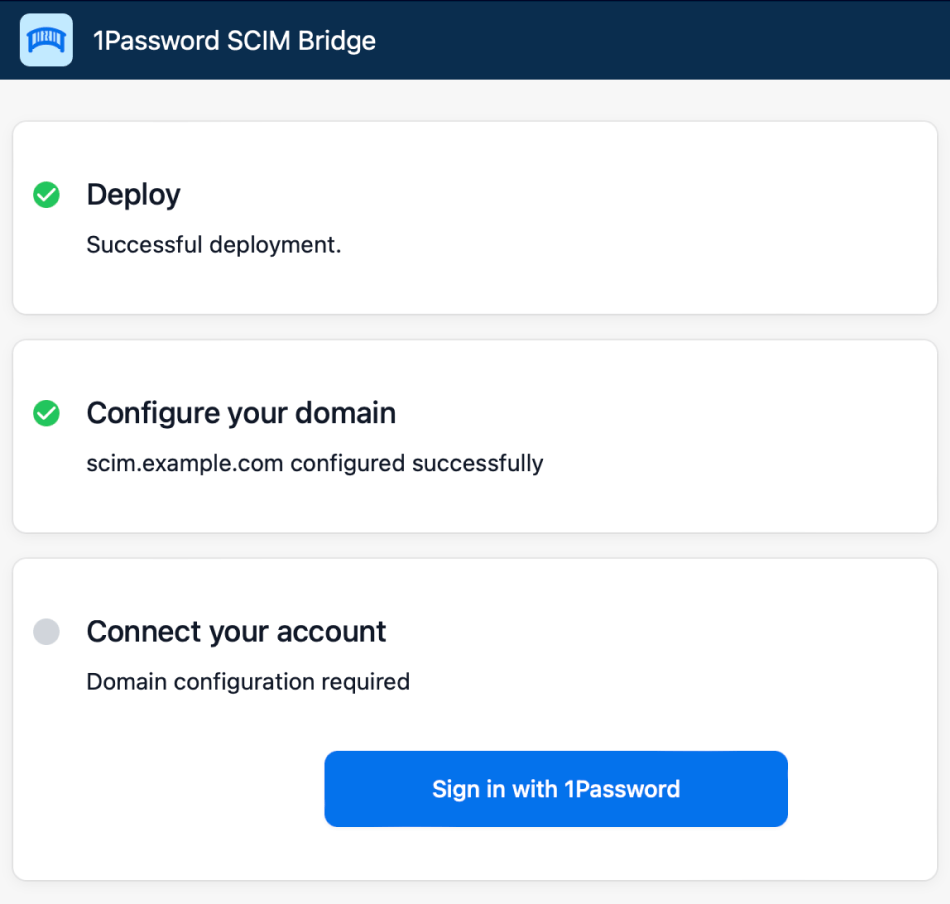
2.1: Melde dich bei deinem 1Password-Konto an
Auf der 1Password SCIM Bridge-Setup-Seite:
- Gib den Domainnamen ein, den du für die SCIM-Bridge konfiguriert hast, um ihn zu verifizieren.
- Klicke auf Anmelden und folge den Anweisungen auf dem Bildschirm.
Erfahre, was du tun kannst, wenn du die Details einer bestehenden Bereitstellungsintegration siehst.
2.2: Authentifiziere dich mit der SCIM-Bridge
Nachdem du den Einrichtungsprozess abgeschlossen hast, erhältst du eine scimsession-Datei und ein Bearer-Token. Speichere sie beide in 1Password, falls du sie erneut benötigst.
- Klicke auf <yourdomain> installieren. Du wirst die Statusseite der 1Password SCIM-Bridge sehen.
- Gib dein OAuth-Bearer-Token ein und wähle Verifizieren.
Wichtig
Das Bearer-Token und die scimsession-Datei, die du bei der Einrichtung erhältst, können zusammen verwendet werden, um auf Informationen aus deinem 1Password-Konto zuzugreifen. Du musst das Bearer-Token mit deinem Identitätsanbieter teilen. Allerdings solltest du es niemals an andere Personen weitergeben. Außerdem solltest du deine scimsession-Datei niemals an andere weitergeben.
2.3: Konfiguriere eine statische IP-Adresse
Wenn du die 1Password SCIM Bridge zum ersten Mal einsetzt, wird ihr eine temporäre IP-Adresse zugewiesen. Es ist nicht garantiert, dass diese Adresse konstant bleibt, wodurch die automatische Bereitstellung unterbrochen werden kann.
Um die SCIM-Bridge ohne Unterbrechung nutzen zu können, musst du die öffentliche IP der 1Password SCIM-Bridge auf eine statische IP-Adresse umstellen. Hier erfährst du, wie du eine statische IP-Adresse konfigurierst.
Schritt 3: Verbinde deinen Identitätsanbieter mit der 1Password SCIM Bridge
Wichtig
Wenn du bereits 1Password Business verwendest, solltest du sicherstellen, dass die E-Mail-Adressen und Gruppennamen in deinem 1Password-Konto mit denen deines Identitätsanbieters übereinstimmen.
- Wenn jemand eine andere E-Mail-Adresse in 1Password verwendet, bitte ihn oder sie, diese zu ändern.
- Falls du bereits bestehende Gruppen in 1Password hast, die du mit Gruppen in deinem Identitätsanbieter synchronisieren möchtest, passe die Gruppennamen in 1Password an.
Da die 1Password SCIM-Bridge einen SCIM 2.0-kompatiblen Webservice bietet, der OAuth-Bearer-Token zur Autorisierung akzeptiert, kannst du sie mit einer Vielzahl von Identitätsanbietern nutzen.
Verbinde dich mit dem TLS-gesicherten API-Gateway, Proxy oder Load Balancer, auf dem du die SCIM-Bridge konfiguriert hast (zum Beispiel: https://scim.example.com) und authentifiziere dich mit deinem OAuth-Bearer-Token.
Benutzerhandbuch
Erfahre, wie du deinen Identitätsanbieter verbinden kannst:
Unterstützung erhalten
Hol dir Hilfe bei der SCIM-Bridge, zum Beispiel wenn du dein Bearer-Token oder deine Sitzungsdatei verloren hast.
Wenn du eine bestehende Bereitstellungsintegration hast
Wenn du auf der Einrichtungsseite die Details für eine bestehende Bereitstellungsintegration siehst, wähle die Option Anmeldedaten neu generieren und folge dann den Schritten, um die neuen Anmeldedaten in deinem 1Password-Konto zu speichern und sie auf deiner SCIM-Bridge zu installieren. Bestehende Einstellungen für die Integration, wie z. B. die von dir ausgewählten verwalteten Gruppen, werden beibehalten.
Wenn du vorhandene Einstellungen nicht beibehalten musst, wähle Weitere Aktionen > Bereitstellung deaktivieren. Wähle dann auf der Einrichtungsseite erneut Anmelden aus.
Um weitere Hilfe zu erhalten oder Feedback zu geben, kontaktiere den 1Password Business Support oder nimm an der Diskussion mit der 1Password Support Community teil.
Mehr erfahren
War dieser Artikel hilfreich?
Freut mich, das zu hören! Wenn du etwas hinzufügen möchtest, zögere nicht, uns zu kontaktieren.
Tut mir leid, das zu hören. Bitte kontaktiere uns, wenn du uns mehr darüber erzählen möchtest.